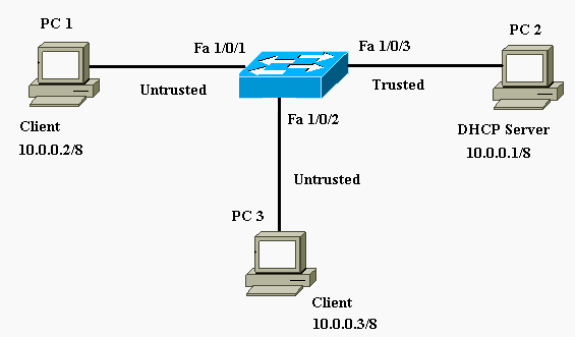
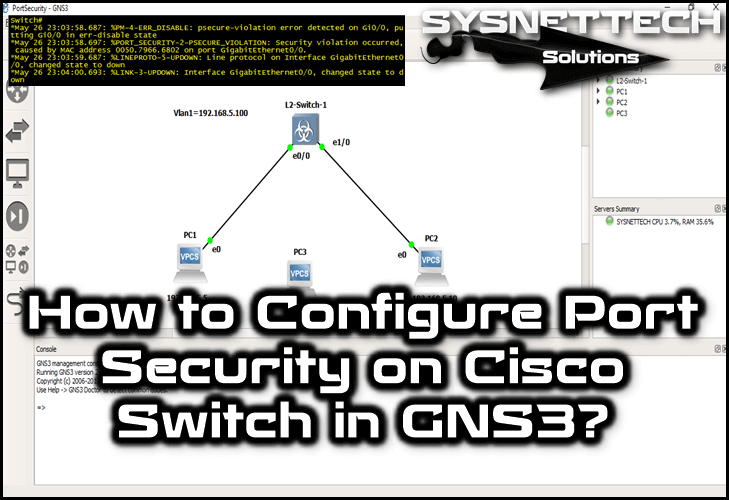
Port Security Configuration on Cisco switch using packet tracer – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber- Security Network-Security Online

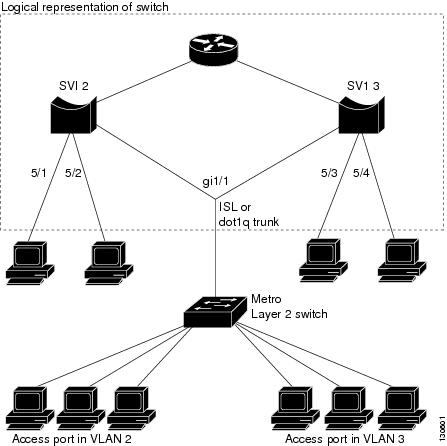
Switch Port Security Access Control List (ACL) Configuration on Cisco... | Download Scientific Diagram

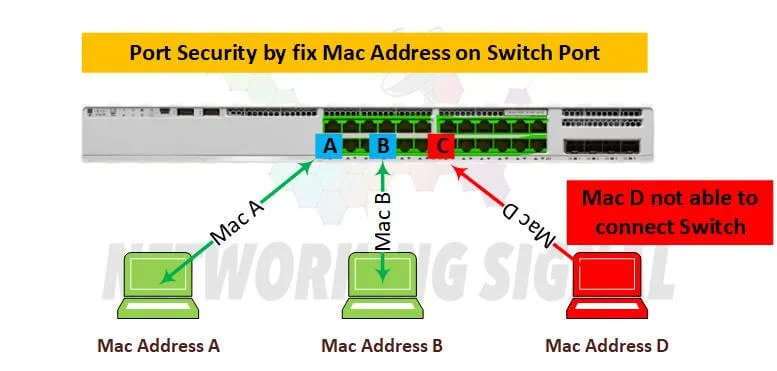
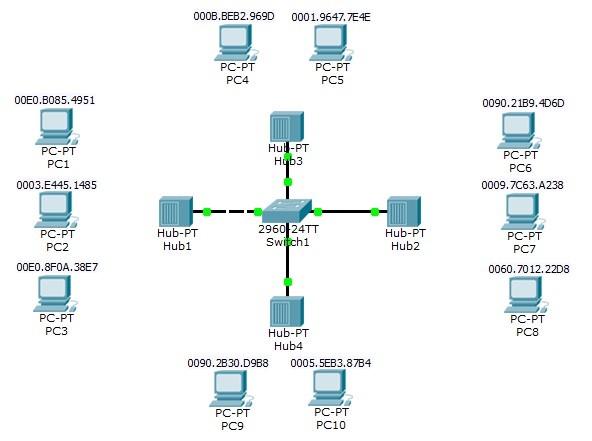
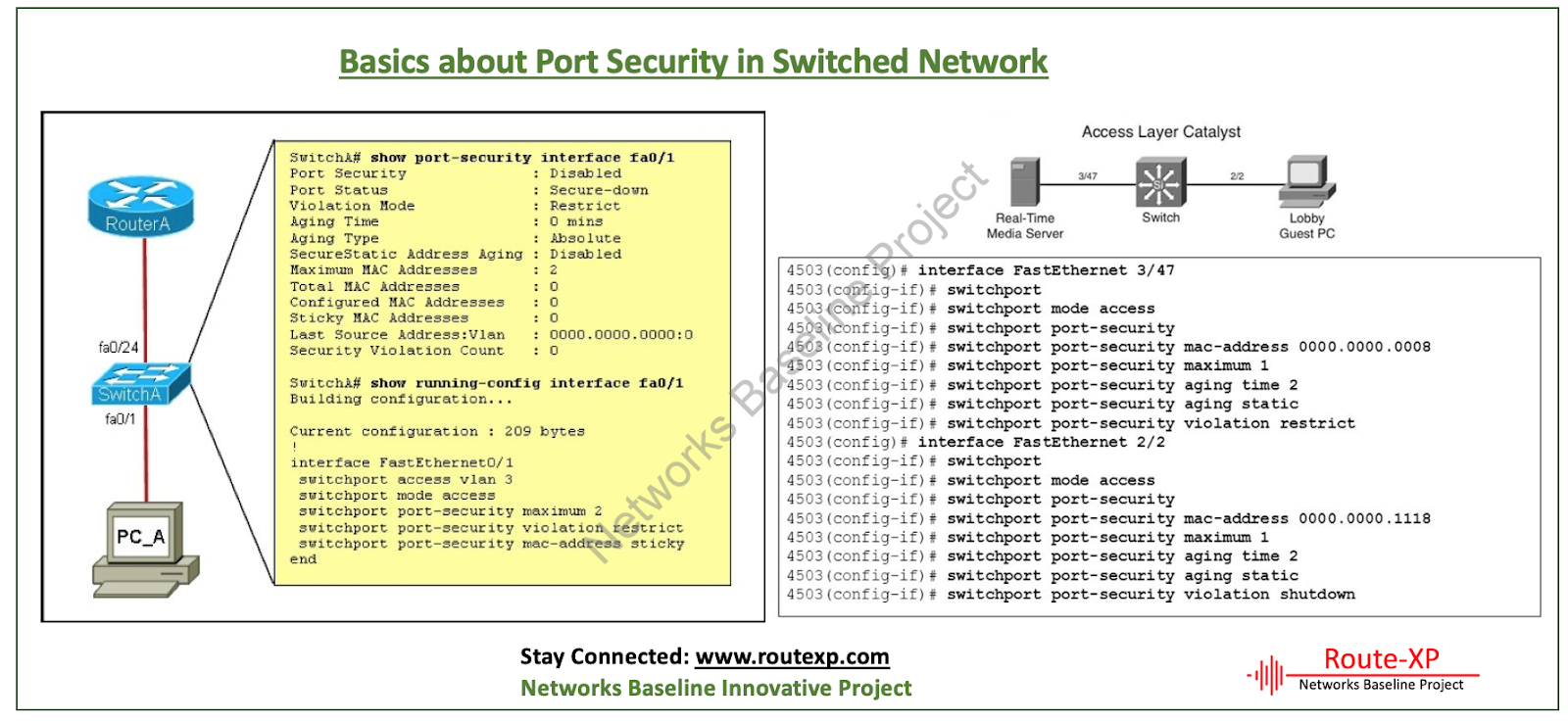
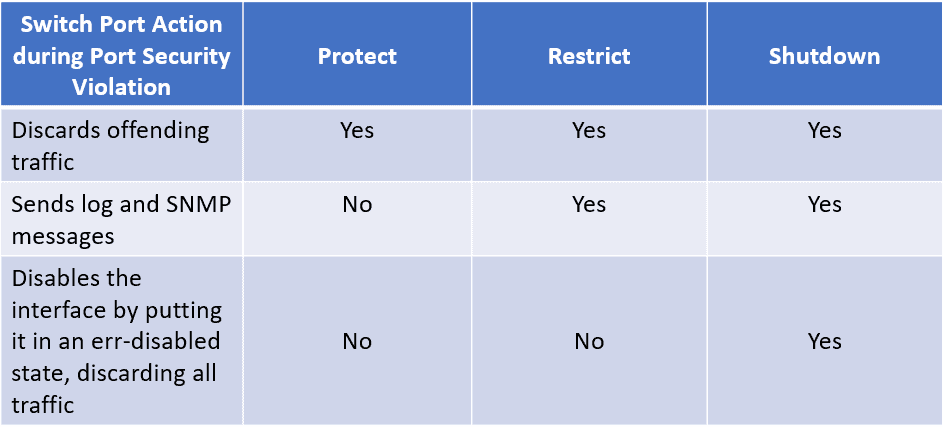
port security:Learn how to secure cisco switches ports using switchport – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online